Imagine this: You're managing a fleet of IoT devices spread across the globe, and you need to access them remotely for troubleshooting or maintenance. But how do you ensure that your connections are secure, efficient, and compliant with industry standards? Enter AWS IoT and SSH—a powerful combo that can revolutionize the way you manage your devices.
Let’s be real here—IoT is no longer just a buzzword. It’s a game-changer for businesses, developers, and tech enthusiasts alike. But with great power comes great responsibility, especially when it comes to security. Accessing IoT devices through SSH on AWS isn’t just about convenience; it’s about safeguarding your infrastructure from potential threats.
In this guide, we’ll dive deep into the world of IoT SSH access on AWS, breaking down the steps, best practices, and tools you need to make it happen. Whether you're a seasoned pro or just starting out, this article has got you covered. So grab your coffee, sit back, and let’s get into it!
Read also:Somali Raaxo Telegram 2025 The Ultimate Guide To Stay Connected
Table of Contents
Introduction to Accessing IoT via SSH on AWS
Understanding IoT and Its Importance
What is SSH and Why Use It on AWS?
Setting Up SSH Access for IoT Devices on AWS
Best Practices for Securing IoT SSH Connections
Common Issues and Troubleshooting Tips
Read also:Somali Wasmo 2025 The Ultimate Guide To Understanding And Exploring
Tools and Techniques for Efficient IoT Management
Scaling Your IoT SSH Infrastructure on AWS
Managing Costs When Using SSH on AWS
Future Trends in IoT and SSH Integration
Introduction to Accessing IoT via SSH on AWS
So, you’ve heard about IoT (Internet of Things) and SSH (Secure Shell), but what happens when you combine the two on AWS? Think of it like giving your devices superpowers—remote access, secure communication, and seamless management. AWS provides a robust platform to handle all of this, making it easier than ever to manage your IoT fleet.
Before we jump into the nitty-gritty, let’s clarify why SSH on AWS is such a big deal. SSH offers encrypted connections, ensuring that your data remains safe from prying eyes. When integrated with AWS IoT, it becomes a powerful tool for managing devices at scale. Plus, AWS’s cloud infrastructure ensures reliability and scalability, which are crucial for any IoT deployment.
Now, let’s break it down step by step. In the following sections, we’ll explore the basics of IoT and SSH, set up your environment, discuss security best practices, and even touch on some troubleshooting tips. By the end of this guide, you’ll be a pro at accessing IoT devices via SSH on AWS.
Understanding IoT and Its Importance
Let’s start with the basics. IoT, or the Internet of Things, refers to a network of interconnected devices that can communicate and share data. These devices range from smart thermostats and wearables to industrial sensors and autonomous vehicles. The beauty of IoT lies in its ability to gather real-time data and automate processes, saving time and resources.
But why is IoT so important? In today’s data-driven world, businesses need actionable insights to stay competitive. IoT provides a wealth of data that can be analyzed to improve operations, enhance customer experiences, and drive innovation. However, with great power comes great responsibility, and that’s where security comes in.
Enter SSH—a protocol designed to secure network communications. By using SSH on AWS, you can ensure that your IoT devices are protected from unauthorized access and cyber threats. This is especially crucial when dealing with sensitive data or critical infrastructure.
Key Benefits of IoT Integration
- Real-time data collection and analysis
- Remote monitoring and control
- Automated processes for efficiency
- Scalability to accommodate growing needs
What is SSH and Why Use It on AWS?
SSH, or Secure Shell, is a cryptographic network protocol that allows secure communication between devices over an unsecured network. It’s like a secret handshake that ensures only authorized users can access your systems. When combined with AWS, SSH becomes an indispensable tool for managing IoT devices.
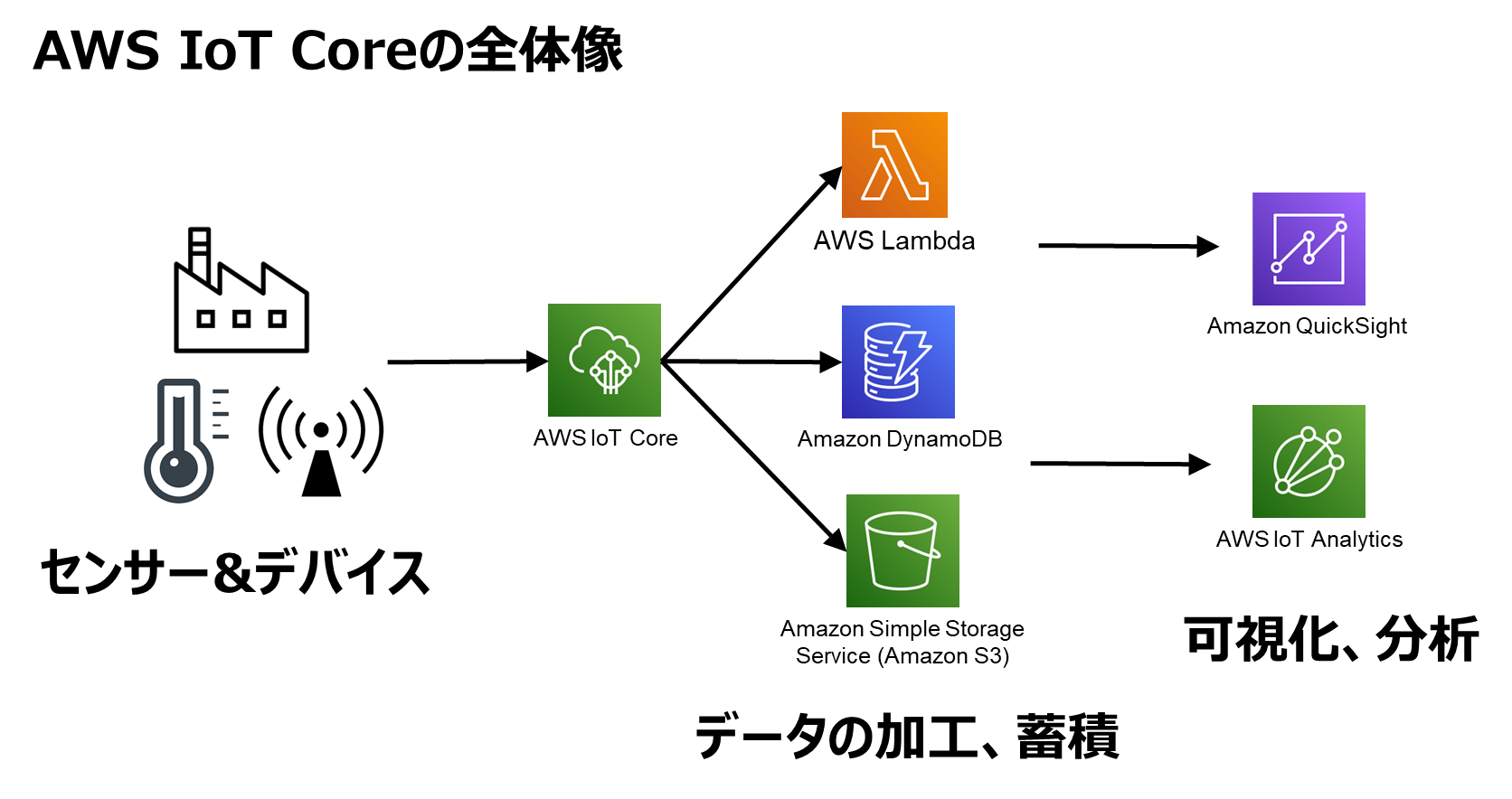
AWS offers a range of services that make SSH integration seamless. For instance, AWS IoT Core provides a managed service for connecting, monitoring, and interacting with IoT devices at scale. By leveraging SSH, you can remotely access these devices for troubleshooting, configuration, and maintenance—all while maintaining a high level of security.
But why choose AWS for SSH? Here are a few reasons:
- Scalable infrastructure to handle large-scale IoT deployments
- Advanced security features to protect your data
- Integration with other AWS services for a comprehensive solution
- Global presence with data centers in multiple regions
How SSH Works on AWS
At its core, SSH works by establishing an encrypted connection between two devices. When you use SSH on AWS, you’re essentially creating a secure tunnel that allows you to interact with your IoT devices without exposing sensitive information. AWS provides tools like IAM roles and security groups to further enhance this security.
Setting Up SSH Access for IoT Devices on AWS
Alright, let’s get our hands dirty and set up SSH access for your IoT devices on AWS. Don’t worry—it’s not as complicated as it sounds. Follow these steps, and you’ll be up and running in no time.
Step 1: Create an AWS Account
If you don’t already have one, sign up for an AWS account. It’s free to start, and you can explore the platform without committing to paid services. Once you’re logged in, navigate to the AWS Management Console.
Step 2: Set Up AWS IoT Core
Next, head over to AWS IoT Core and create a new thing. This represents your IoT device and serves as the entry point for SSH access. Make sure to assign it a unique identifier and configure any necessary settings.
Step 3: Configure Security Settings
Security is paramount when dealing with IoT devices. Use AWS IAM to create roles and policies that define who can access your devices. Additionally, set up security groups to control inbound and outbound traffic.
Step 4: Install SSH on Your Devices
Finally, install an SSH client on your IoT devices. This allows them to communicate securely with AWS. Popular options include OpenSSH and PuTTY, depending on your operating system.
And there you have it—a fully functional SSH setup for your IoT devices on AWS. Easy peasy, right?
Best Practices for Securing IoT SSH Connections
Now that you’ve set up SSH access for your IoT devices, it’s time to focus on security. Here are some best practices to keep your connections safe:
- Use strong, unique passwords for each device
- Enable two-factor authentication (2FA) for added security
- Regularly update your devices and software to patch vulnerabilities
- Limit access to trusted IP addresses or networks
- Monitor logs for suspicious activity and take action if needed
Remember, security is an ongoing process. Stay vigilant and keep your systems up to date to protect against emerging threats.
Advanced Security Features
AWS offers several advanced security features to further enhance your IoT SSH setup. These include:
- Encryption for data in transit and at rest
- Identity and access management (IAM) for fine-grained control
- CloudTrail for auditing and monitoring
Common Issues and Troubleshooting Tips
Even the best-laid plans can go awry, so let’s talk about some common issues you might encounter when accessing IoT devices via SSH on AWS.
Issue 1: Connection Refused
If you’re unable to establish a connection, double-check your security settings. Ensure that the necessary ports are open and that your device is reachable from the internet.
Issue 2: Authentication Failed
Authentication issues are often caused by incorrect credentials or misconfigured policies. Verify that your username and password are correct and that your IAM roles are properly set up.
Issue 3: Slow Performance
Slow performance can be a sign of network congestion or resource limitations. Optimize your setup by using AWS CloudFront for caching and load balancing.
Tools and Techniques for Efficient IoT Management
To make the most of your IoT SSH setup on AWS, consider using these tools and techniques:
- AWS IoT Device Defender for monitoring and auditing
- CloudWatch for real-time monitoring and alerting
- Automated scripts for routine tasks and maintenance
These tools can help streamline your operations and reduce the workload on your team. Plus, they integrate seamlessly with other AWS services, creating a cohesive ecosystem for managing your IoT devices.
Scaling Your IoT SSH Infrastructure on AWS
As your IoT fleet grows, so will your infrastructure. AWS makes it easy to scale your SSH setup to accommodate additional devices and users. Use AWS Auto Scaling to automatically adjust resources based on demand, ensuring optimal performance at all times.
Additionally, consider using AWS Lambda for serverless computing. This allows you to execute code in response to events without managing servers, freeing up time and resources for other tasks.
Managing Costs When Using SSH on AWS
Cost management is crucial when working with AWS. Use AWS Cost Explorer to track your expenses and identify areas for optimization. Set up budget alerts to ensure you stay within your financial limits.
Also, consider using reserved instances or spot instances for cost-effective resource allocation. These options can significantly reduce your expenses while maintaining performance.
Future Trends in IoT and SSH Integration
Looking ahead, the integration of IoT and SSH on AWS is poised to evolve rapidly. Expect advancements in areas like:
- Edge computing for faster data processing
- Machine learning for predictive maintenance
- Quantum encryption for next-level security
Stay ahead of the curve by keeping up with the latest trends and innovations in the IoT and cloud computing space.
Conclusion and Next Steps
And there you have it—a comprehensive guide to accessing IoT devices via SSH on AWS. By following the steps and best practices outlined in this article, you can create a secure, efficient, and scalable setup for managing your IoT fleet.
Remember, the key to success lies in staying informed and proactive. Keep learning, experimenting, and adapting to new technologies and trends. And don’t forget to share your experiences and insights with the community—knowledge is power!
So, what are you waiting for? Get out there and start building your IoT empire. The future is yours for the taking!